8th Annual Cyber
Security Summit
15-16 October, 2025
Berlin

Speakers
Summit will host speakers from the world’s leading companies

Conrad Reisch
Head of Strategy, Partnerships and Adoption


Jonathan Robinson
Director Insider Threat

Nicol Daňková
Head of SOC


Steve Williamson
Audit Account Director, Information Security and Data Privacy


José Hermida
Head of IT Cyber Defense Technologies


Ahmed Nasr
Operations Director Egypt and Director Milk Africa & Turkey


Khaled Elsharkawy
Integrated Supply Chain Senior Director


Mueen Uddin Siddique
Senior Director – Access Network Procurement


Chamath Nawaratne
VP & CPO Middle East &Africa


Shannon Hore
Senior Vice President Procurement and Logistics


Sandeep Sharma
Director Group Procurement & International Markets Supply Chain

Hottest topics
More details about what will be discussed this annual
New Lessons Learned
New Opportunities Unlocked
New Lessons Learned
New Opportunities Unlocked


Look at the Main Topics
Of Our Conference
- 01Understanding Social Engineering Attacks: The Psychology Behind the Threat
- 02Digital Infrastructure Threats: IoT, Supply Chains, and Cloud Computing at Risk
- 03TDIR & Insider Threats Lifecycle
- 04Edge Computing and 5G: A New Frontier for Cybersecurity Risks
- 05From Prevention to Prediction. Cyber Security Revolution
- 06Automating Security Excellence. SCA and ASCA in Modern Cyber Defence
Early bird tickets available
Month of early booking discounts
Discount
20 %
Discount
10 %
Discount
0 %
Testimonials
What our users say about our conferences
Our Clients
"We partner with top professionals to provide creative ideas, inspiration and guidance"






























Sponsors
Our trusted sponsors



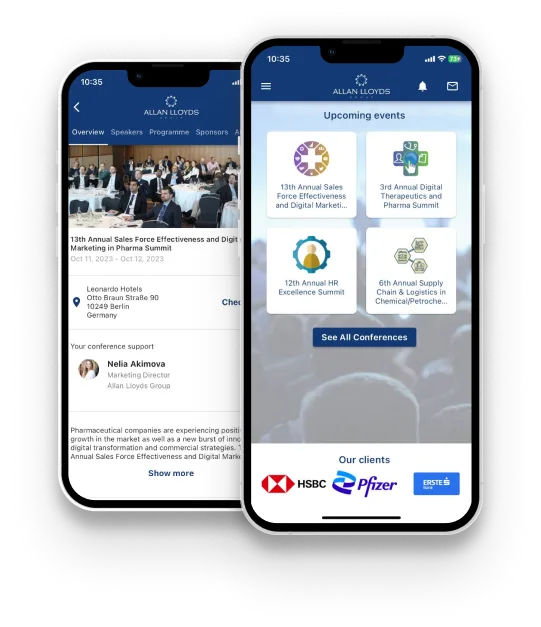
Download our App to
Enhance Your Event Experience
This innovative app is aimed at enhancing your networking experience through a seamless blend of interaction and connectivity. We have carefully crafted this application with new features that empower you to make the most out of your engagements, ensuring personalised experiences and seamless networking opportunities.